What Is Virtual Patching in WordPress? How It Works and Why It Matters

Most hacked WordPress sites have one thing in common: an outdated plugin.
Sometimes, updates get ignored. Sometimes, they’re delayed on purpose to avoid breaking something. And sometimes, they’re just missed, especially when one person is managing multiple sites. But that delay, even if unintentional, gives attackers a window to exploit.
In 2024, there were 7,966 new vulnerabilities in the WordPress ecosystem—a 34% jump compared to 2023. The majority of those were found in plugins, not core files or themes. And many didn’t have a patch available when they were first reported.
Virtual patching is a layer of security that keeps sites secure in moments like these, when updates can’t happen fast enough or don’t exist yet.
In this blog, we’ll discuss virtual patching in WordPress, why it’s important, how it works, and when should site managers use it.
What Is Virtual Patching?
Virtual patching is a security method that blocks known exploits before they reach vulnerable code without making any changes to the application itself. It works by analyzing incoming HTTP requests and filtering out malicious patterns at the network or application layer, usually through a Web Application Firewall (WAF) or Intrusion Prevention System (IPS). OWASP defines this technique as a “security policy enforcement layer which prevents the exploitation of a known vulnerability.”
In practice, this means that if a plugin has a known SQL injection or cross-site scripting vulnerability, a virtual patch can intercept and block the exact request signature that would exploit it. These patches are written as targeted rules that match specific payloads, unlike generic WAF filters that often rely on broader pattern detection. Because these rules are vulnerability-specific, they tend to be more accurate and generate fewer false positives.
The patch itself is deployed “externally” to the application. That could be in the form of a reverse proxy, a cloud-based WAF, or a plugin that injects PHP-level filters before WordPress fully loads. This makes it effective even in zero-day situations, where the vulnerability is being exploited in the wild, but an official fix hasn’t yet been released.
In those cases, security companies with threat intelligence pipelines can push out a virtual patch within hours, giving developers more time to test and apply updates safely.
Why Is Virtual Patching More Effective Than Malware Scanning in WordPress?
Malware scanners detect problems after they’ve already happened. They scan files or monitor behavior to identify signs of infection, but they don’t prevent the initial exploit.
Virtual patching stops the exploit from executing in the first place.
Malware scanners can miss threats if malware is obfuscated or designed to evade detection. They also consume server resources and may produce false positives, especially when scanning frequently.
This should not be overlooked: scanning repeatedly every file for malware means the plugin reads everything on your site. This puts heavy load on CPU, memory, and disk especially on shared hosting for a very low added value, unless you know that your website has been corrupted. This is well explained in the article Why everything you know about your WordPress Malware Scanner is wrong.
Virtual patching doesn’t rely on file changes or behavioral analysis. It blocks known exploit patterns at the request level, using targeted rules linked to confirmed vulnerabilities. This makes it faster, more accurate, and better suited for live protection.
How Does Virtual Patching Work?
When a plugin vulnerability is discovered, it usually gets documented with a CVE (Common Vulnerabilities and Exposures) ID. That’s where everything starts. Security researchers—or platforms like Patchstack—verify the vulnerability and document exactly how the exploit works.
That becomes the virtual patch.
This patch isn’t a code-level fix. It’s a security rule added to a firewall or intrusion prevention system that blocks specific types of requests known to trigger the vulnerability.
As mentioned before, these rules are tightly scoped. Instead of broadly guessing what might be malicious, they look for the exact attack patterns tied to the vulnerability. That could mean blocking a certain payload in a URL parameter, restricting unexpected POST data, or filtering out known injection strings.
For example, say a plugin has a vulnerability that allows attackers to inject SQL via a custom id parameter. A virtual patch for that issue might allow only numeric input for that parameter and block anything else—without touching the plugin or breaking site functionality.
Once deployed, the patch prevents the exploit from reaching your application. Your plugin is still technically vulnerable, but the attack can’t run. It just gives you time to test the update, get approvals, or wait for the developer to release a proper fix, whether you are working on a single or multiple sites.
Why Virtual Patching Matters For Your Agency
Managing WordPress sites at scale means dealing with plugin vulnerabilities on a regular basis. Some are low-risk and easy to patch. Others show up in popular plugins used across dozens of your client sites, and that’s where things get tricky.
You can’t always patch immediately. Maybe the fix hasn’t been released yet. Or the update exists, but you need time to test it. Maybe the plugin is part of a custom workflow that would break if updated without review. Until you sort that out, the vulnerable code stays live.
That delay matters. Attackers don’t wait for your test window. If a known vulnerability is being actively exploited, and the plugin hasn’t been updated, your site is exposed. If you’re using the same plugin across several installs, that one issue can become a network-wide problem.
Virtual patching fills that gap. It blocks the specific type of request that would exploit the vulnerability without touching the plugin itself. The code is still vulnerable, but the attack can’t go through. You stay protected while buying time to plan the update properly.
This is especially helpful when you’re juggling a portfolio of sites. Instead of reacting to every new vulnerability like it’s an emergency, you can roll out updates on your timeline—without leaving things wide open in the meantime.
It’s not a replacement for updating. But it is what makes staying secure feel manageable.
How WP Umbrella Handles Virtual Patching
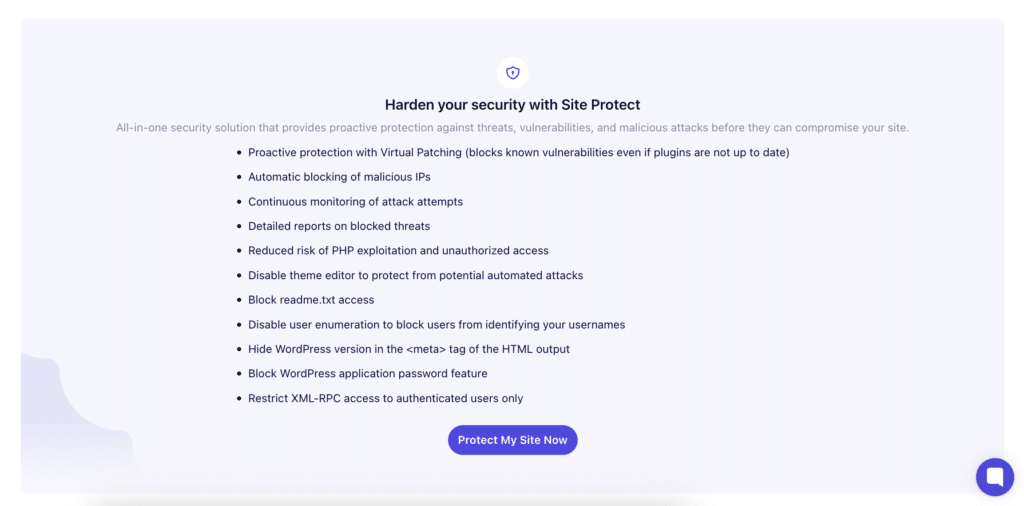
WP Umbrella scans your WordPress sites every six hours. If there’s a known vulnerability in a plugin, theme, or core file, it flags it in your dashboard so you can act on it early.
For added security, it offers virtual patching, powered by Patchstack, as an add-on. If you’ve purchased and enabled the Site Protect add-on, WP Umbrella will block known exploit attempts at the PHP level using rules from Patchstack. These rules are based on real-world attack patterns, so they don’t rely on generic filters or guesswork.
The Site Protect add-on replaces the need for multiple security plugins by offering features like virtual patching, disabling file editors, preventing user enumeration, and adding smart security headers. It applies patches automatically as new threats are identified. You don’t have to configure anything. And if the same vulnerable plugin appears across multiple sites, all of them are covered without needing to switch between dashboards.
The pricing is also straightforward. If you purchase virtual patching before the end of June 2025, it’s $2/month per site. After that, it goes up to $3/month. And you only pay for the sites where it’s turned on.
Virtual patching sits alongside WP Umbrella’s other security features: alerts for SSL and domain expiration, visual changes, PHP errors, and overall site health. Everything is tracked in a single dashboard and is built for people managing dozens of WordPress sites.
Can Site Protect Replace my Security Plugin?
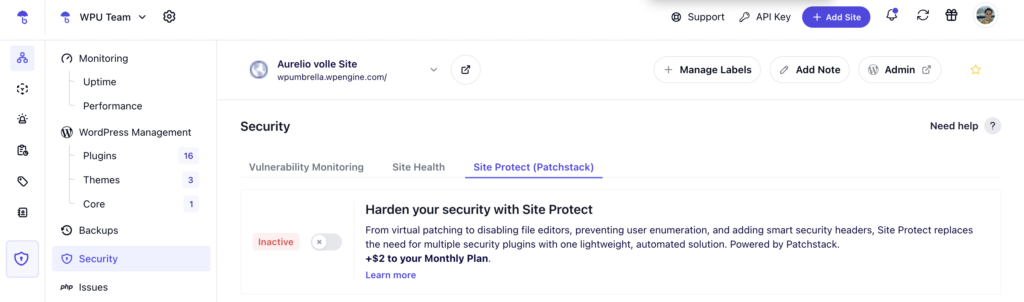
If you’re using Site Protect (our security add-on powered by Patchstack), you can remove security plugins like SecuPress or Wordfence in most cases.
Site Protect includes virtual patching and automatically blocks known vulnerabilities before they’re exploited. This makes malware scanning and bulky firewalls unnecessary.
These older plugins often consume a lot of server resources and act only after a threat has compromised the site, while Site Protect works proactively.
On top of that, most hosting providers already have server-level malware detection tools like Imunify360 in place, which means you’re often duplicating effort and draining resources by running less powerful on-site scanners
Patch When You Can—But Protect Always
Vulnerabilities are part of managing WordPress sites. Some can be fixed right away. Others take time.
Virtual patching helps you stay protected during that in-between phase.bUse WP Umbrella’s virtual patching add-on, powered by Patchstack, to automatically apply patches based on verified vulnerabilities. It’s not a shortcut. It’s a way to reduce the pressure when timelines and security don’t line up.
FAQs About Virtual Patching
Virtual patching is a security method that blocks known exploit attempts without changing the underlying code. It works by intercepting malicious requests before they can reach vulnerable parts of your application.
A regular update fixes the vulnerable code itself. A virtual patch doesn’t touch the code. It blocks specific requests that try to exploit the vulnerability, acting as a temporary layer of protection.
Security researchers analyze the vulnerability and identify the type of request used to exploit it. They then write targeted rules that match that pattern and block it at the firewall or application level.
Sometimes, yes—if the vulnerability is identified and a patch rule is created based on early threat intelligence. However, virtual patching still relies on known exploit behavior, so speed and visibility are key.
No. The virtual patching add-on works at the PHP level and only applies rules that match the vulnerabilities found in your installed plugins or themes. There’s no unnecessary overhead.
No. Virtual patching is available as a paid add-on. If you enable it, WP Umbrella will automatically deploy protection rules based on verified vulnerabilities.
It’s $2/month per site if you activate it before the end of June 2025. After that, the price goes up to $3/month.
