Stop WordPress Vulnerabilities Before They’re Exploited: Meet Site Protect

In 2024, Patchstack found 7,966 vulnerabilities across the WordPress ecosystem. That includes plugins your clients still rely on, and in many cases, haven’t updated.
If you’re responsible for keeping those sites safe, you know how fast a small oversight can turn into a late-night fire drill.
Site Protect, powered by Patchstack, helps you stop those issues by proactively securing your websites even when plugins/themes/WordPress core aren’t updated.
Let’s take a closer look at how this add-on works, and why almost 3,000 websites have already started using it.
Why malware scanners alone aren’t enough for agency workflows
Most WordPress security plugins still sell peace of mind through malware scanning. But once you understand how these scanners work, and how easily they can be bypassed, that peace of mind starts to feel pretty fragile.
Let’s start with the basics. There are two kinds of scanners:
- Local scanners (like WordFence or NinjaScanner) run inside your WordPress site.
- Remote scanners (like MalCare or Virusdie) send your files to an external app through a plugin for analysis.
They take different approaches, but the core limitation is the same: they impact performance, and they tell you if something bad has already happened. And even that’s not a guarantee.
With local scanners, you’re relying on a WordPress plugin to inspect the same environment that malware is already running in. If that sounds risky, it is.
Once malware is active, it can tamper with the scanner itself, disabling it, whitelisting itself, or feeding it clean-looking data. In some cases, it doesn’t even leave a trace. A scanner might return a clean report, but only because the malware told it what to say.
Remote scanners are harder to fool, but not impossible. They rely on a local plugin to collect data and send it to their external scanner. If malware can intercept or alter that data before it’s sent, the result is the same: false negatives, missed threats, and a very real risk slipping past unnoticed, as well as an impact on your server bandwidth.
Sophisticated malware often hides in plain sight. Instead of using obvious patterns like base64_decode, it assembles its malicious behavior at runtime using dynamic strings or variables. Most scanners rely on static analysis: they look for known bad patterns in your files. They can’t see what code will do when it runs.
The result? Clean scans but compromised sites.
Some malware executes once, completes its task (like injecting a backdoor or exporting user data), then deletes itself immediately. Unless your scanner runs in the exact same moment, down to the millisecond, it might never be able to detect the threat. By the time the scan runs, it’s already gone.
So, should you uninstall your malware scanner?
Not necessarily. Scanners still have a role, especially against low-effort attacks. But if scanning is the only thing protecting your client sites, you’re gambling on a flawed system.
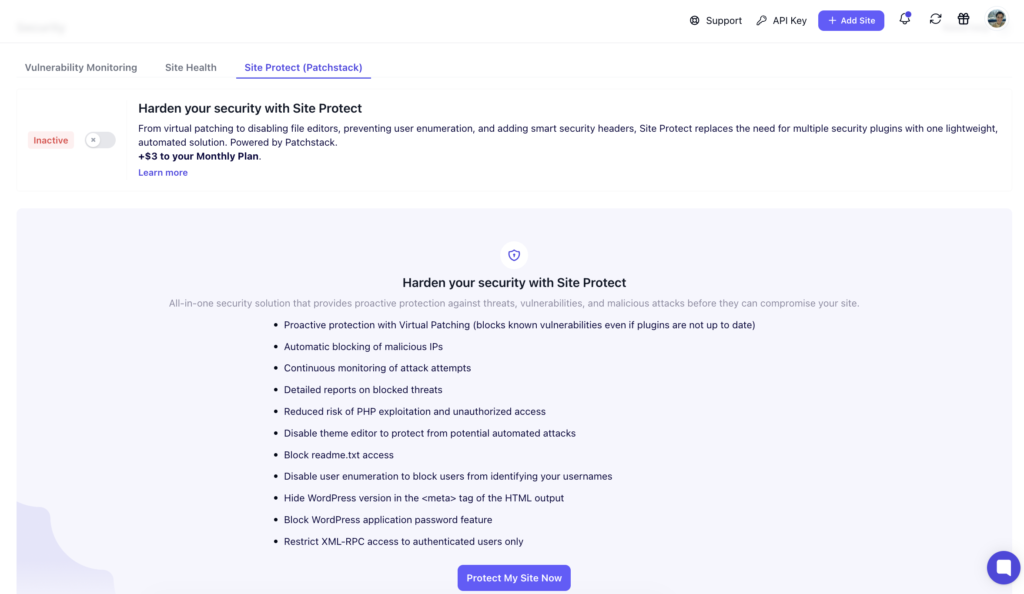
That’s why Site Protect takes a different approach. Powered by Patchstack, it uses something called virtual patching. Instead of looking for malware after it’s been uploaded, Site Protect blocks known vulnerabilities from being exploited in the first place, even if the plugin or theme is still unpatched.
Let’s say a plugin has a SQL injection vulnerability tied to a specific parameter. Site Protect applies a rule that blocks that exact attack pattern, at the PHP level, before WordPress even fully loads. The plugin stays technically vulnerable, but the exploit never lands.
This is what makes Site Protect different: it doesn’t rely on alerts and doesn’t overload your server. It shields your client sites during the exact window of disclosure and update, where most attacks happen.
How Site Protect helps agencies stay ahead of known vulnerabilities
- Blocks known plugin vulnerabilities before they’re exploited
Most agencies don’t update plugins the moment a patch comes out. Sometimes there’s a testing backlog, sometimes the fix introduces new issues. Meanwhile, attackers aren’t waiting. As soon as a vulnerability becomes public, exploit attempts tend to spike.
Site Protect closes that window. When a vulnerability is confirmed, it applies a rule that blocks the exact exploit, even if the plugin hasn’t been updated yet. These rules come directly from Patchstack’s threat feed and are deployed without touching any code. The vulnerability still exists, technically, but the attack gets stopped at runtime.
That gives you time to plan updates on your terms, instead of rushing them under pressure.
- Doesn’t slow down your site
Security shouldn’t be something you have to configure or constantly monitor. With Site Protect, there are no settings to tweak or performance trade-offs to consider. Once it’s on, it handles vulnerability protection automatically, without scanning files, loading extra scripts, or adding server pressure. It works at the PHP level, quietly blocking known exploits without getting in the way of your workflows.
- Doesn’t break WordPress site’s functionality
It’s one thing to block threats. It’s another to do it without causing problems for the people using the site. Site Protect focuses only on confirmed vulnerabilities and applies highly targeted rules. No overreaching firewalls, no false positives, and no broken contact forms. Your sites keep working the way they should with fewer ways in for attackers.
What’s included in Site Protect
Site Protect combines real-time virtual patching with a set of hardening rules that cover common attack vectors. Here’s an overview of what it adds when enabled:
| Features | What It Does | Why It Matters |
| Vulnerability Virtual Patching Firewall | Automatically blocks known vulnerabilities in WordPress core/themes/plugins and common attack vectors. | Prevents exploits before updates are applied or released. This helps you to protect your websites from new malwares and common attacks |
| Disable Theme/File Editors | Removes built-in editors from the WP admin | Prevents attackers from injecting malicious code (and your clients from doing crazy stuff) |
| Block readme.txt / WP version meta | Hides WordPress version info | Avoids being targeted by bots |
| Disable User Enumeration | Stops attackers from discovering usernames | Defends against brute-force logins |
| Restrict XML-RPC Access | Allows XML-RPC only for authenticated users | Reduces spam and attack surface |
| Security Headers | Adds headers like X-Frame-Options, X-XSS-Protection | Defends against clickjacking, XSS, and more |
| Block debug.log & sample config files | Prevents access to sensitive information from the debug.log file | Keeps internal configs private |
| Disable Index Views | Blocks directory listing | Prevents accidental file exposure |
| Block Proxy Comment Posting | Disables comments via third-party services | Reduces spam and abuse attempts |
How to enable Site Protect
Step 1: Upgrade to a WP Umbrella premium plan
Site Protect is only available to premium users. If you’re on the free plan, the first step is to upgrade. Once you’ve switched, the Site Protect add-on becomes an option in your dashboard. Learn more about WP Umbrella’s pricing.
Step 2: Enable Site Protect from the dashboard
Open the site you want to protect in WP Umbrella and head to the Security tab. There you’ll see the toggle for Site Protect. Activating it adds the feature for $2/month/site.
Step 3: Security hardening
After activation, there’s nothing else you need to configure. Site Protect works in the background, rules are updated in real time, and protections run continuously at the PHP level. Your client reports will also include a dedicated section showcasing how Site Protect proactively secures their websites even when plugins aren’t updated.
Final thoughts
Keeping WordPress sites secure is an ongoing job, and the pressure usually falls on the people managing updates and client expectations. Site Protect doesn’t replace those responsibilities, but it gives you breathing room. Vulnerabilities get blocked before they can be used, sites keep running normally, and you’re not left scrambling when a patch isn’t ready or a client delays approval.
Thousands of websites are already running with Site Protect enabled. It takes a few clicks to switch on, and from then on, the rules update in the background without you needing to check in. If you’re already using WP Umbrella, it’s a straightforward step: go to your dashboard, navigate to the website’s security section, and turn the toggle on.
Turn on Site Protect now.
Next, read a complete guide to selling site protection to clients.
Source: Patchstack
