Top 10 WordPress Security Issues [+ How to Avoid Them]

WordPress powers nearly half the web for a good reason, but this popularity comes at a price—the price of keeping it safe. One weak plugin, an outdated theme, or a lazy password, and your site becomes an easy target.
In this guide, we’ll walk you through the 10 most dangerous security holes threatening your WordPress site today and show you how to patch them.
Top 10 WordPress Security Issues and Fixes
1. Vulnerabilities in Plugins and Themes
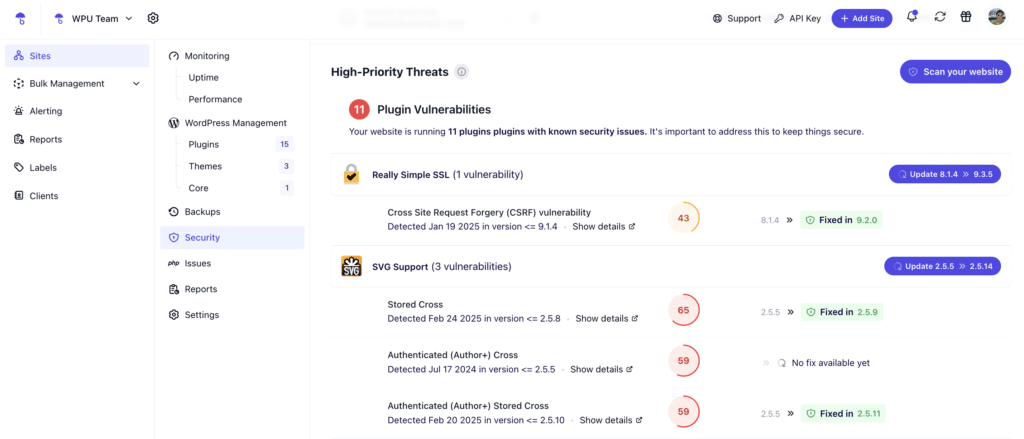
Outdated plugins and themes create the perfect entry point for hackers.
When security vulnerabilities are discovered in WordPress components, they’re quickly publicized and patched—but if you’re not updating, you’re leaving your door open to attacks.
And this isn’t a WordPress problem specifically. WordPress’s popularity makes it a prime target for security researchers and hackers alike. It’s not because WordPress is unsafe; it’s because it’s popular. The more widely used a platform is, the more closely it’s examined.
Regular updates also prevent compatibility issues that can degrade your site’s performance, potentially leading to compromised data, broken functionality, and frustrated visitors.
How to avoid plugin vulnerabilities:
- Set a routine to check for plugin, theme, and core updates. Or better yet, turn on automatic updates in WordPress to take one more task off your plate.
- Only install plugins and themes from the official WordPress repository or well-known developers. That way, you know they’re actively maintained—and far less likely to leave you exposed.
- If a plugin or theme isn’t in use, remove it. Even inactive plugins can be exploited if they’re outdated or poorly maintained.
- Use a WordPress management tool like WP Umbrella to simplify your entire maintenance workflow. It’s a great plugin to back up your website, monitor uptime and performance, schedule automated scans for vulnerabilities, detect PHP issues, and more.
Also read: 5 Tools To Scan WordPress Sites for Vulnerabilities
2. Brute Force Attacks
Brute force attacks are what they sound like. It’s the relentless login attempts by bots trying thousands of username and password combinations until they break in.
Since there are bots behind these attacks, they are fast, automated, and dangerous. A weak password like “ADMIN123” can be cracked in seconds. Worse, repeated login attempts can overload your server or lock out real users.
How to avoid brute force attacks:
- Use strong, unique passwords for all accounts.
- Enable two-factor authentication (2FA) for an extra layer of protection. According to Melapress, 41% of WordPress users don’t use 2FA or strong passwords.
- Block IPs after 3-5 failed tries to stop the endless guessing game.
- Add a CAPTCHA to your login page to stop automated attacks by the bots.
- Use a security plugin to monitor logins and block suspicious IPs automatically.
3. Cross-Site Scripting (XSS) Attacks
In 2023, XSS accounted for 53.3% of all new vulnerabilities in the WordPress ecosystem, making it the most common exploit type. XSS attacks inject malicious scripts into your site’s front end through forms, comment sections, and other user inputs. The code runs in the browser of anyone who visits the compromised page—often without detection.
Attackers use XSS to steal cookies, session tokens, and sensitive user data. They can impersonate users, redirect them to phishing pages, or take over accounts. These attacks often go unnoticed and can cause significant damage before they’re caught.
How to avoid XSS attacks:
- Install a trusted security plugin or use a Web Application Firewall (WAF) to detect and block XSS attempts in real-time.
- Validate and sanitize all user inputs and outputs. Never trust data from forms, URLs, or external sources without proper filtering.
- Add Content Security Policy headers to your site to control which scripts can be executed and from which sources.
- Follow secure coding standards by escaping output and sanitizing inputs to prevent malicious code injection.
- Perform regular code audits to identify and patch weak points in your theme or plugin files.
- Schedule penetration tests to proactively uncover and fix vulnerabilities before attackers can take advantage.
4. Unrestricted XML-RPC Protocol
The XML-RPC protocol, a legacy feature in WordPress, was initially introduced to allow remote communication between WordPress and external apps. Back when mobile publishing and offline blogging tools were in demand, XML-RPC made it possible to post content remotely.
However, as WordPress evolved—particularly with the introduction of the REST API in 2015—this older protocol became largely obsolete. Despite this, XML-RPC remains active by default on all WordPress installations, opening the door to several serious security risks.
One of the major concerns is its potential for abuse in brute-force attacks. Unlike traditional login attempts that can be easily flagged and blocked, XML-RPC enables attackers to bundle hundreds of login requests into a single HTTP call.
Additionally, the pingback feature tied to XML-RPC can be weaponized for DDoS attacks, flooding a target site with traffic through a network of hijacked WordPress sites.
How to avoid XML-RPC exploits:
- Most modern plugins and applications now use the REST API, so XML-RPC is often unnecessary. Disabling it closes a major loophole.
- Use a plugin to block access to xmlrpc.php. Security plugins like Wordfence or Disable XML-RPC make it easy to shut down access without needing to edit server files.
- Manually block xmlrpc.php via .htaccess. If you’re comfortable editing server settings, add a rule to deny all access to this file—it’s a lightweight and effective solution.
- If specific plugins or services still require XML-RPC, consider limiting its features or whitelisting particular IPs.
5. SQL Injection Vulnerabilities
SQL injection is one of the oldest and most dangerous attack methods used against websites. It happens when a website doesn’t properly validate user input and accidentally passes that input directly into an SQL query.
This lets attackers inject their commands into the database—commands that were never meant to run. If successful, they can view private data, change site content, create new users, or even delete entire tables.
In WordPress, SQL injection usually targets vulnerable plugins or themes—especially those that accept form submissions or URL parameters and don’t sanitize input. Hackers often automate these attacks, scanning the internet for sites with weak points.
And if multiple apps share the same database, one vulnerable site can put all of them at risk. At its worst, an SQL injection can escalate from a data breach to a full server compromise, depending on how permissions are configured.
How to prevent SQL injection vulnerabilities:
- Sanitize all inputs—never trust user input, especially from forms, search bars, or URL strings.
- Use prepared statements with parameterized queries. Also, avoid directly embedding variables into the query string if you’re writing custom SQL.
- Keep plugins and themes updated. Many SQL injection flaws come from outdated or poorly coded third-party components.
- Only grant your database user the permissions it needs. Don’t give it full access unless it’s required.
- Use a security plugin to scan for vulnerable code and block known SQL injection patterns.
- Run regular vulnerability scans to catch flaws before an attacker does.
6. Exposing Your wp-config.php File
It’s 2025, and you’d think this wouldn’t still be a problem—but it is. One of WordPress security’s most common (and dangerous) oversights is leaving the wp-config.php file exposed. This single file contains everything from your database credentials to secret keys and essential configuration settings.
Attackers actively look for this file because, with access to it, they can inject malicious scripts, manipulate your site’s behavior, steal data, or even delete your site entirely.
Sometimes, this file is accidentally made public by misconfigured servers or overly permissive file permissions. And yes—sometimes it’s even indexed by Google.
How to prevent exposing wp-config.php file:
- Move wp-config.php one level above your web root directory. WordPress will still find it, but the public won’t.
- Set file permissions to 400 or 440 to keep it readable by the server.
- Block web access to the file using .htaccess (for Apache) or server rules (for Nginx).
- Use strong security keys—you can generate fresh ones from WordPress’s official key generator.
- Disable PHP error reporting in production to avoid leaking paths or credentials in error messages.
- Back it up regularly (along with your whole site) so you can recover if anything goes wrong.
7. Lack of Regular Site Backups
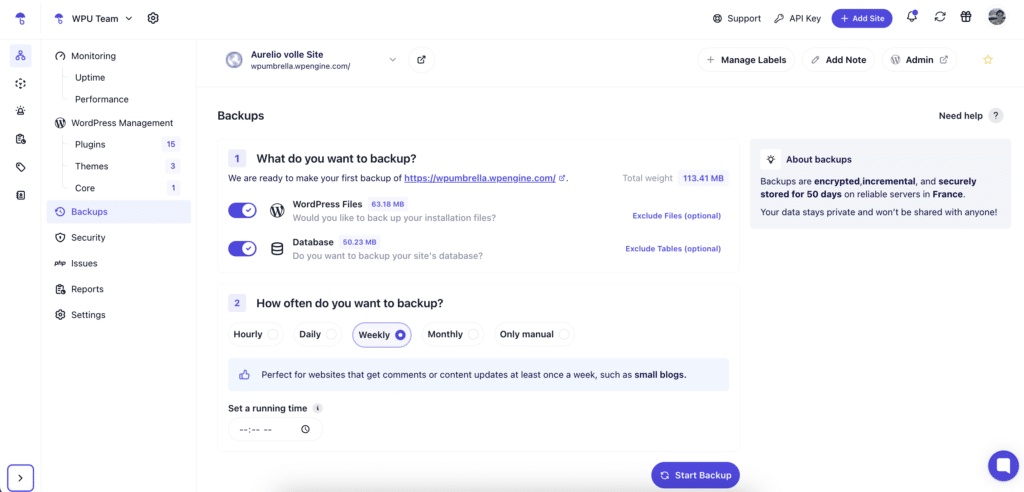
This isn’t a vulnerability in the traditional sense, but it’s just as critical. If your site gets hacked, crashes, or breaks during an update, and you don’t have a backup, you’ll have to start from zero.
No backups = no recovery.
It doesn’t matter how secure your site is if you can’t bring it back when something goes wrong.
What makes this worse is that most people only realize the importance of WordPress backups after something goes wrong. Either they assumed their host was handling it (many don’t), or they were doing manual backups every once in a while and never tested them. Both are risky.
How to avoid this:
- Automate your backups, and don’t leave it up to memory. Set them to run on a schedule—daily for active sites and weekly for static ones.
- Use a reliable tool like WP Umbrella. It’s a solid option as it offers incremental backups, so only the changes are saved after the first full backup. This means less server load and faster performance.
- Follow the 3-2-1 rule: maintain at least three backups stored in two different formats with one copy kept offsite.
- Keep several versions. If your last backup was after malware hit, you’ll want to roll back to a clean version before that.
- Know how to restore. A backup is useless if you don’t know how to bring your site back up quickly.
Related: 8 Best WordPress Backup Plugins
8. DDoS Attacks
A Distributed Denial of Service (DDoS) attack is a method used by attackers to overwhelm a website’s server with an excessive amount of traffic, rendering it inaccessible to legitimate users. This is achieved by using multiple compromised systems, often forming a botnet, to send a flood of requests to the target server.
These botnets can consist of various devices, including computers and Internet of Things (IoT) devices, which have been infected with malware to operate under the attacker’s control.
A DDoS attack’s primary objective is to disrupt a website’s normal functioning, causing downtime and potentially leading to financial losses and reputational damage. Hackers use it for various reasons, including extortion, competitive advantage, political motives, or to cause disruption.
How to avoid DDoS attacks:
- Use a Web Application Firewall (WAF). Cloudflare and Sucuri offer WAFs that filter out malicious traffic before it reaches your server.
- Use a Content Delivery Network (CDN). CDNs distribute your website’s content across multiple servers globally, helping to absorb and mitigate traffic surges during an attack.
- Regularly analyze your website’s traffic to identify unusual spikes that could indicate the onset of a DDoS attack.
- Configure your server to limit the number of requests a user can make within a specific timeframe to reduce the impact of potential attacks.
- Ensure your hosting provider offers DDoS mitigation services as part of their package.
9. Weak Passwords and Login Credentials
Weak passwords and default login details are still one of the easiest ways for attackers to break into a WordPress site. Brute force attacks or credential stuffing, using leaked login info from other data breaches, both rely on one thing: bad password hygiene.
If you’re still using “admin” as a username or “password123” as your login, you’re handing over access without much of a fight. And if that account has admin-level access, attackers can take complete control—install malware, steal data, and deface your content.
This kind of attack doesn’t require advanced skills, just time and a botnet. And once they’re in, the cleanup can be a mess—reputation loss, downtime, or worse.
Passwords are a low-effort fix with a high-impact payoff.
How to prevent it:
- Use long, complex passwords (12+ characters with upper/lowercase, numbers, and symbols).
- Ditch the “admin” username. Create something unique and remove the default.
- Enable 2FA for all admin users. This blocks most brute force attempts cold.
- Install a password manager (like Bitwarden or KeePass) to generate and store strong credentials.
- Limit login attempts, so bots get locked out after a few tries.
- Change passwords immediately if you’ve had a breach or even a suspicion of one.
10. Poor User and Permission Management
This might sound obvious, but it bears repeating because it’s often overlooked. Human error is still one of the biggest reasons behind hacking incidents.
One of the easiest ways to open your site to risk is by giving users more access than they need. The consequences can be serious if an account with high-level access is hacked. It could result in SEO spam injections, unauthorized access to sensitive data, malware installations, and even phishing campaigns hosted on your site.
How to avoid this issue:
- Only give users the exact level of access they need—nothing more.
- Regularly audit your user list and remove any accounts that are no longer active or necessary.
- Downgrade permissions when roles change. If a user no longer needs admin rights, reduce their access immediately.
Conclusion
Keeping your site secure takes regular attention. The good news? You don’t have to tackle this alone.
WP Umbrella makes it simple to handle most of the security threats we’ve discussed.
Plugin and Theme Vulnerabilities: WP Umbrella scans your websites every 6 hours for vulnerabilities, so you get alerts before issues turn serious. With its bulk update feature, you can keep all your plugins and themes current across multiple sites with just a few clicks.
Comprehensive Backup System: The automated incremental backup system is GDPR-compliant and stores your data securely for 50 days. Its one-click restoration means you can retrieve your data quickly.
Uptime and Performance Monitoring: Security issues often manifest as performance problems first. WP Umbrella’s uptime and performance tracking lets you spot unusual activity before it escalates into a full-blown security crisis.
Proactive Security Alerts: Instead of waiting for something to break, WP Umbrella actively monitors your sites for potential security vulnerabilities, sending alerts directly to your inbox or Slack when action is needed.
Whether you’re managing a single WordPress site or hundreds, WP Umbrella gives you the tools to stay ahead of security threats. Because when it comes to WordPress security, prevention isn’t just better than cure; it’s everything!
FAQs: WordPress Security Issues
Common WordPress security issues include vulnerable plugins and themes, brute force attacks, XSS, SQL injections, and poor user permission management. Keeping your site updated and using tools like WP Umbrella can help you stay protected.
To prevent WordPress REST API security issues, disable unused API endpoints, require authentication for sensitive actions, and sanitize all API inputs. Using security plugins or a firewall can also block unauthorized access attempts.
Yes. WordPress plugin security issues are one of the leading causes of hacks. Use only well-reviewed plugins from trusted sources, keep them updated, and remove any you’re not actively using to reduce exposure.
Warning signs include slow loading, spammy content, login issues, and unexpected traffic spikes. Regular scans with tools like WP Umbrella can detect performance and uptime issues early before they escalate.
Security plugins are a strong first line of defense, but no tool is 100% foolproof. They help block common threats, detect malicious activity, and enforce strict login rules, but regular updates, backups, and good password practices are still essential.
